What is Buffer Overflow Full Defination.
Buffers are memory storage regions that temporarily hold data while it's being transferred from one location to a different .
A buffer overflow (or buffer overrun) occurs when the quantity of knowledge exceeds the storage capacity of the memory buffer.
As a result, the program attempting to write down the info to the buffer overwrites adjacent memory locations.
For example, a buffer for log-in credentials could also be
designed to expect username and password inputs of 8 bytes, so if a
transaction involves an input of 10 bytes (that is, 2 bytes quite expected), the program may write the surplus data past the buffer boundary.
Buffer overflows can affect all kinds
of software.
They typically result from malformed inputs or failure to
allocate enough space for the buffer. If the transaction overwrites
executable code, it can cause the program to behave unpredictably and
generate incorrect results,
access errors, or crashes.
What is a Buffer Overflow Attack
Attackers
exploit buffer overflow issues by overwriting the memory of an
application. This changes the execution path of the program, triggering a
response that damages files or exposes private information.
for instance , an attacker may introduce extra code, sending new instructions to
the appliance to realize access
thereto systems.
If attackers know the memory layout of a program,
they will
intentionally feed input that the buffer cannot store, and overwrite
areas that hold executable code, replacing it with their own code.
for instance , an attacker can overwrite a pointer (an object that points
to a different area in memory) and point it to an exploit payload,
to realize control over the program.
Types of Buffer Overflow Attacks
Stack-based
buffer overflows are more common, and leverage stack memory that only
exists during the execution time of a function.
Heap-based attacks are harder
to hold out and involve flooding the memory space allocated for a program beyond memory used for current runtime operations.
What Programming Languages are More Vulnerable?
C and C++ are two languages that are highly
vulnerable to
buffer overflow attacks, as they don’t have built-in safeguards against
overwriting or accessing data in their memory. Mac OSX, Windows, and
Linux all use code written in C and C++.
Languages
like PERL, Java, JavaScript, and C# use built-in safety mechanisms that minimize the likelihood of buffer overflow.
How to Prevent Buffer Overflows
Developers can protect against buffer overflow vulnerabilities via security measures in their code, or by using languages
that provide built-in protection.
In addition, modern operating systems have runtime protection. Three common protections are:
Address space randomization (ASLR)—randomly moves round the address space locations of knowledge regions. Typically, buffer overflow attacks got to know the locality of executable code, and randomizing address spaces makes this virtually impossible.
Data
execution prevention—flags certain areas of memory as non-executable or
executable, which stops an attack from running code
during a non-executable region.
Structured
exception handler overwrite protection (SEHOP)—helps stop malicious
code from attacking Structured Exception Handling (SEH), a built-in
system for managing hardware and software exceptions. It thus prevents
an attacker from having the ability to form use of the SEH overwrite exploitation technique. At a functional level, an SEH overwrite is achieved employing a stack-based buffer overflow to overwrite an exception registration record, stored on a thread’s stack.
Security measures in code and
OS protection
aren't enough. When
a corporation discovers a buffer overflow vulnerability, it must react quickly to patch the affected software and
confirm that users of the software can access the patch.

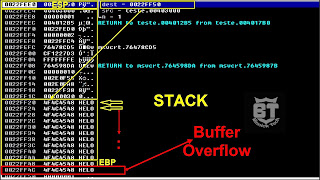
Overview
A buffer overflow condition exists when a program attempts to place more data during a buffer than it can hold or when a program attempts to place data during a memory area past a buffer. during this case, a buffer may be a sequential section of memory allocated to contain anything from a personality string to an array of integers. Writing outside the bounds of a block of allocated memory can corrupt data, crash the program, or cause the execution of malicious code
Buffer Overflow Attack Example
[Adapted from “Buffer Overflow Attack Explained with a C program Example,” Himanshu Arora, June 4, 2013, The Geek Stuff]
In some cases, an attacker injects malicious code into the memory that has been corrupted by the overflow. In other cases, the attacker simply takes advantage of the overflow and its corruption of the adjacent memory. for instance , consider a program that requests a user password so as to grant the user access to the system. within the code below, the right password grants the user root privileges. If the password is wrong , the program won't grant the user privileges.
printf ("\n Correct Password \n");
pass = 1;
}
if(pass)
{
/* Now Give root or admin rights to user*/
printf ("\n Root privileges given to the user \n");
}
return 0;
However, there's an opportunity of buffer overflow during this program because the gets() function doesn't check the array bounds.
Here is an example of what an attacker could do with this coding error:
$ ./bfrovrflw
Enter the password :
hhhhhhhhhhhhhhhhhhhh
Wrong Password
Root privileges given to the user
In the above example, the program gives the user root privileges, albeit the user entered an incorrect password. during this case, the attacker supplied an input with a length greater than the buffer can hold, creating buffer overflow, which overwrote the memory of integer “pass.” Therefore, despite the wrong password, the worth of “pass” became non zero, and therefore the attacker receives root privileges.
Buffer Overflow Solutions
To prevent buffer overflow, developers of C/C++ applications should avoid standard library functions that aren't bounds-checked, like gets, scanf and strcpy.
In addition, secure development practices should include regular testing to detect and fix buffer overflows. the foremost reliable thanks to avoid or prevent buffer overflows is to use automatic protection at the language level. Another fix is bounds-checking enforced at run-time, which prevents buffer overrun by automatically checking that data written to a buffer is within acceptable boundaries.
Veracode Helps Identify Buffer Overflows
Veracode’s cloud-based service identifies code vulnerabilities, like buffer overflow, in order that developers can address them before they're exploited.
![Validate my Atom 1.0 feed [Valid Atom 1.0]](valid-atom.png)











0 Comments